Securing web applications using Burp Suite and OWASP Juice Shop
A tutorial on testing, securing and learning about web security through Burp Suite and OWASP Juice Shop
You might have heard of a recent controversy wherein a “hacker” obtained access to the Social Security Numbers of a few individuals in the Missouri state government.


However, it turns out this “hacker” was a reporter, who simply viewed HTML code on a web page. And the SSNs were clearly visible within the HTML code. No - the numbers were not encrypted!
In general, it is extremely important to secure web apps. Insecure web apps could lead to stolen credentials. Or act as a gateway to the rest of an organization’s network leading to severe data breaches, and loss of public trust in the long run. Burp Suite is the go to tool for web app testing. Burp Suite is installed by default on Kali Linux (just like most other cybersecurity tools - Kali Linux is a real game changer!).
You can start off by opening a Temporary project on Burp Suite.
Burp Suite has multiple key features. I’m going to focus on Proxy, Target, Repeater, and Intruder for this tutorial.
Proxy: Funnels traffic to Burp Suite
Target: As the name implies - identify the target web app
Repeater: Send repeated requests or modification of previously sent requests
Intruder: Mounting attacks on insecure web app authentication fields
OK - let’s get started!
Proxy
In order for Burp Suite to act as a proxy, you need to set up your browser to easily route traffic to and from it. For this, you can install a Firefox web browser extension - ‘FoxyProxy Standard.’ Modify FoxyProxy to add the Burp Suite proxy. By default, the location of the Burp Proxy server is 127.0.0.1. Add this to FoxyProxy, and turn it on as below.
OWASP Juice Shop
OWASP stands for Open Web Application Security Project and they provide a bunch of open-source software project resources. Burp Suite in combination with OWASP is a great way to get started in hands-on web application security.
OWASP has a quirky but awesome website called the OWASP Juice Shop (I’m always craving for a good juice shop - I never found one in the US, and there are tons in India :) ). On the OWASP website, they say:
“OWASP Juice Shop is probably the most modern and sophisticated insecure web application!”
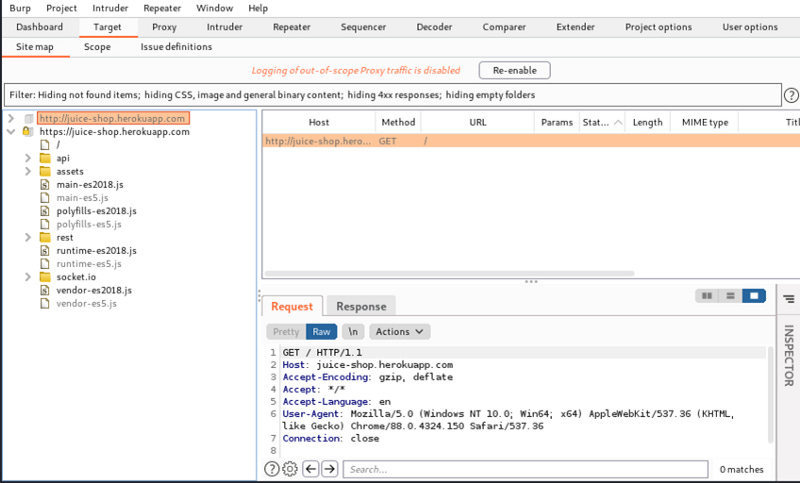
There are multiple ways to start the OWASP Juice Shop including local instances on Docker, or Heroku instances. For conveniences, you can visit https://juice-shop.herokuapp.com/.
After visiting this website, the page will appear as if it is loading constantly. Do not fear - this is because the Burp Suite proxy server is intercepting all traffic.
Target
In the Intercept sub-tab under proxy in Burp Suite, turn off intercept.
Next, in HTTP history, click on the website and ‘add to scope.’
Now explore the website on your browser and go to the target tab. After exploring the web app, you should see the site map of the website.
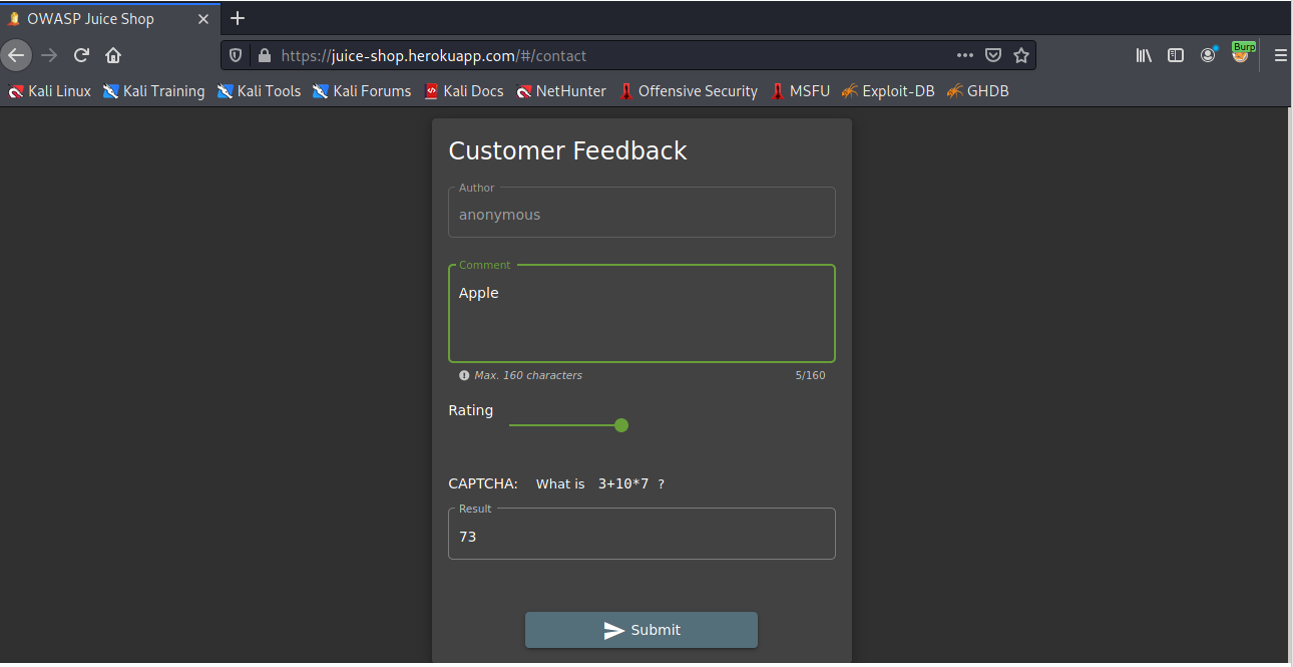
On the main webpage, clicking on the 3 dashes on the left should show you the Customer Feedback option. Click on this.
Next, give some anonymous feedback, as below.
When you visit the Proxy http history on Burp Suite, you should see the post request corresponding to this.
Repeater
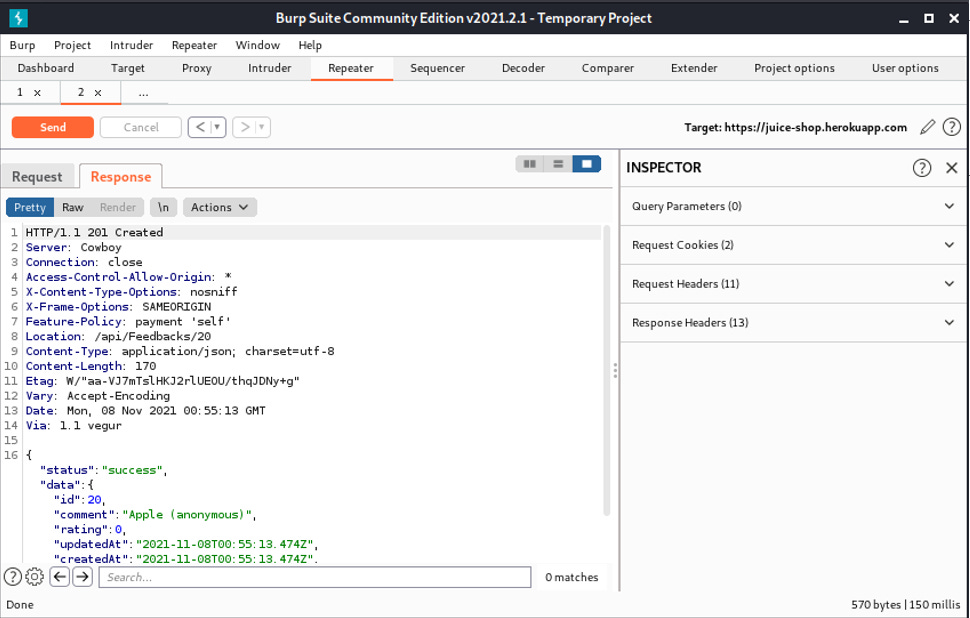
Now, let’s try and modify the customer feedback to give an impossibly low rating of 0 out of 5!
Send this POST request to the repeater, and change the rating value to 0. If the response is a success, then you have successfully sent an extremely low feedback.
I was looking forward to some good, simple, freshly squeezed juice(s) :( .
Intruder
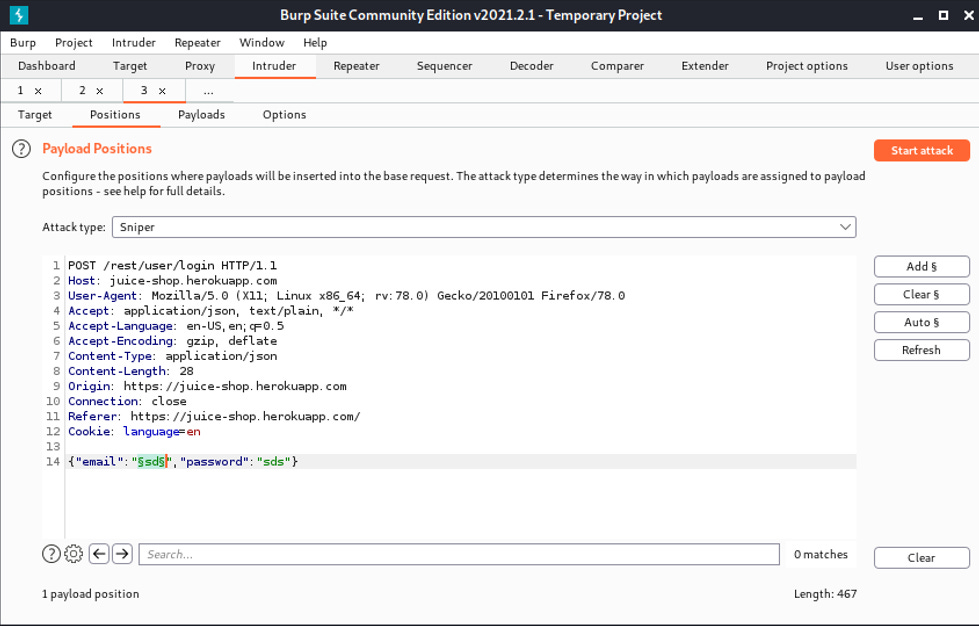
In this section, we are going to try and login as admin. You can find the login button on the top right corner. Choose some random credentials (which will of course not work).
Next, find this post request in the HTTP history, and send to Intruder. Make sure to clear all the highlighted fields, and only choose the email field, and select the Add $ button.
Next, we are going to try SQL injection to force our way into the authentication system. SQL injection takes advantage of the syntax of SQL to inject commands. For example in the case of authentication - SQL queries check usernames and passwords against the list of authenticated users. SQL injection codes could bypass passwords requirements through SQL logic statements. Some standard attacks for default applications are given in this text file: https://github.com/fuzzdb-project/fuzzdb/blob/master/attack/sql-injection/detect/xplatform.txt.
In this example, I copy and paste the .txt document into the Intruder Payload sub-tab, and start the attack.
And success! The attack returns a successful 200 status. The resulting SQL injection code is a' OR 1=1--.
When I run this, I get the following confirmation!
Conclusion
I’ve shown how open access tools Burp Suite and OWASP Juice Shop can be great for learning about and securing web apps. We solved 2 challenges in the OWASP Juice Shop - giving an impossibly low rating, and logging in with the administrator’s account. In doing so, we walked through 4 essential features of securing web apps through Burp Suite: Proxy, Target, Repeater, and Intruder. I hope this was useful.
This post was inspired from TryHackMe and specifically this room: https://tryhackme.com/room/rpburpsuite.
If you enjoyed this week’s post, please share on social media or even just one person you think might enjoy holistic perspectives on the interconnections between technology and modern societies. Feel free to also post any comments in the post discussions on the cyber-physical substack page. This is a small, but growing effort and I hope that I can share in my journey in understanding and building resilient societies.